5 Tools of Every Cyber Threat Intelligence Analyst
Cyber threat intelligence analysts rely on a variety of tools to collect, process, and analyze data that helps organizations defend against cyber threats. These tools enable analysts to swiftly handle emerging risks, identify malicious actors, and proactively mitigate vulnerabilities. In this article, we’ll explore five essential tools that every cyber threat intelligence analyst should be using.
1. Threat Intelligence Feeds
Threat Intelligence (TI) feeds provide real-time data on emerging cyber threats, including indicators of compromise (IOCs) like malicious IP addresses, file hashes, and domains. These feeds are continuously updated and offer insights into ongoing attacks and threat actor behavior.
They help analysts proactively identify risks before they escalate, ensuring that the organization’s defenses are always up to date with the latest threat intelligence. By integrating TI feeds into their workflows, analysts can detect and respond to new threats quickly.
2. Sandbox Environments
A sandbox environment is a safe, isolated space where you can analyze malicious files or URLs without risking network contamination. By observing how malware behaves in real-time, analysts can understand its capabilities, communication patterns, and how it spreads.
ANY.RUN, known for its interactive malware analysis environment, allows analysts to safely detonate malware and monitor every aspect of its execution, from network requests to file system changes. This hands-on approach provides invaluable insights into new and evolving threats.
3. Network Traffic Analysis Tools
Monitoring network traffic is essential for identifying malicious activity. Network traffic analysis tools allow analysts to track anomalous behavior and pinpoint potential cyberattacks. They help TI analysts dissect traffic data to identify suspicious patterns, detect malware communications, and investigate intrusions.
These tools are crucial for understanding how an attack is carried out, what assets are compromised, and how to prevent similar breaches in the future.
4. Dark Web Monitoring Tools
The dark web is a hotspot for cybercriminal activity, where threat actors trade stolen data, malware, and attack services. Dark web monitoring tools allow analysts to track this underground activity and gain early warnings of potential threats to their organizations.
These tools give TI analysts visibility into dark web forums, marketplaces, and communications, helping them identify leaked credentials, sensitive data, or planned attacks targeting their industry or organization.
5. ANY.RUN Threat Intelligence Lookup
Now, let’s dive into one of the most useful tools for TI analysts: ANY.RUN’s Threat Intelligence Lookup.
ANY.RUN’s TI Lookup enables analysts to quickly query detailed information about specific IP addresses, domains, URLs, or file hashes, providing a wealth of data to support threat investigations. This tool accelerates the process of identifying IOCs and understanding the context behind them.
Suppose an organization notices anomalous traffic coming from a specific IP. By entering the IP into ANY.RUN’s TI Lookup, the analyst can retrieve detailed information on whether that IP has been associated with malicious activities like botnets, phishing campaigns, or malware distribution.
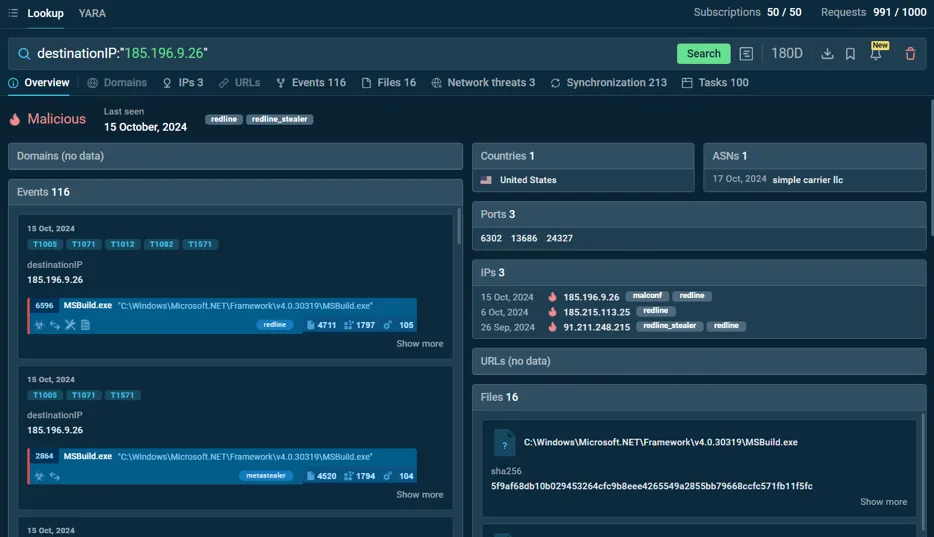
With this intelligence, the organization can take swift action, such as blocking the IP at the firewall level. If you encounter a URL that has triggered a security alert within your organization, you can input it into ANY.RUN’s TI Lookup to gather comprehensive information about its reputation.







